Check out our latest products
If you own a printer from China-based Procolored, watch out: The company’s driver files are full of malware, including a Windows-based backdoor.
Karsten Hahn, a researcher at cybersecurity vendor G Data, reported the findings on Thursday. “A printer company provided infected printer software for half a year,” he said.
Hahn began investigating after YouTuber Cameron Coward at Serial Hobbyism received a printer from Procolored, a provider of direct-to-film printers, which can be used for creating custom T-shirts. While testing the printer for a review, the built-in antivirus Windows Defender and Google’s Chrome browser alerted him of malware threats on his PC.
His computer had been hit with Floxif, a powerful malware that can change Windows executables and install other malicious code. It can also spread itself through connected USB drives. Coward’s PC received the malware alert after installing software from a ZIP folder on the “USB thumb drive Procolored supplied with the printer.”
Although Procolored, a Shenzhen-based company, claimed the malware alerts were false-positives, Coward posted a call on Reddit for a third-party security researcher to double-check. Hahn at G Data began investigating and traced the threat to the printer driver files hosted on Procolored’s website.
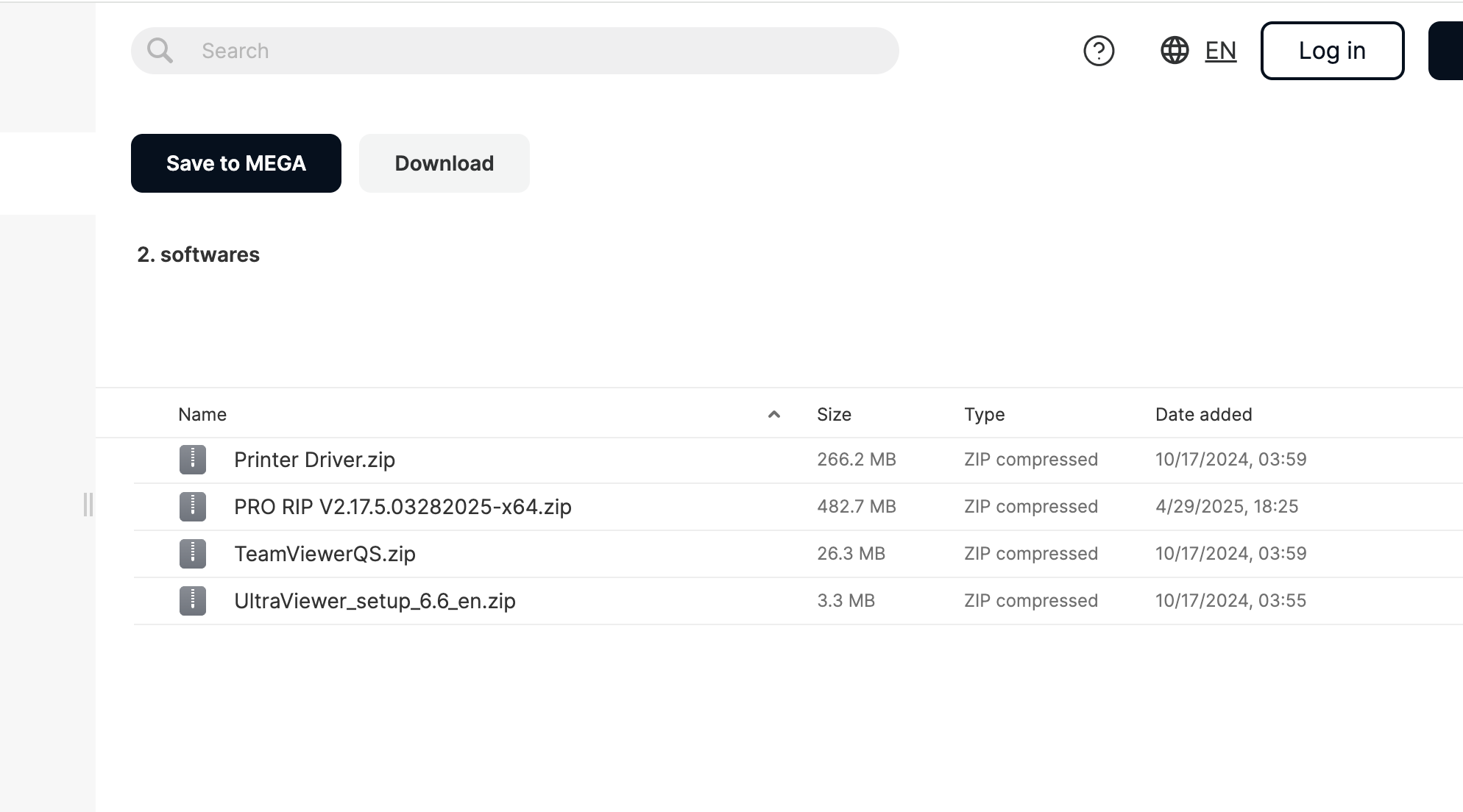
(Credit: Mega.nz/Procolored)
Surprisingly, Procolored continues to host the printer driver files for six products on a third-party Mega.nz file sharing account. Hahn’s antivirus scan found that 39 of the files triggered two malware detections: One for a cryptocurrency wallet stealer, the other a backdoor for Windows PCs dubbed XRed.
Get Our Best Stories!

Stay Safe With the Latest Security News and Updates
By clicking Sign Me Up, you confirm you are 16+ and agree to our Terms of Use and Privacy Policy.
Thanks for signing up!
Your subscription has been confirmed. Keep an eye on your inbox!
Hahn estimates the malicious driver files were circulating for half a year because the Mega.nz directory shows many of the files were last updated about six months ago. His investigation also uncovered evidence that driver files had been originally tampered with on a system that had been “infected several times” with different kinds of malware, which might explain why Hahn’s PC encountered the Floxif infection.
Procolored didn’t immediately respond to a request for comment. But the company told Hahn that it suspects the drivers files were tampered with through an infected USB drive. “The software hosted on our website was initially transferred via USB drives. It is possible that a virus was introduced during this process,” Procolored said.
“As a precaution, all software has been temporarily removed from the Procolored official website,” the company added. “We are conducting a comprehensive malware scan of every file. Only after passing stringent virus and security checks will the software be re-uploaded. This is a top priority for us, and we are taking it very seriously.”
Recommended by Our Editors
The statement also notes that Procolored plans on disclosing the incident to customers and updating its site “once all software has been thoroughly reviewed and confirmed safe.” Hahn says he’s received copies of the new driver files and reports they appear to be clean.
Some might speculate that Procolored deliberately planted the malware. But in his blog post, Hahn wrote, “a far more plausible explanation points to the absence or failure of antivirus scanning on the systems used to compile and distribute the software packages.” That’s because the command-and-control server for the backdoor malware XRed appears to have been offline since February 2024, reducing the threat’s severity.
In the meantime, Hahn recommends affected users consider reinstalling the Windows OS to fully wipe out the threat. “It is possible that some users have dismissed antivirus warnings, assuming the files were safe. This could have allowed the malware to remain undetected,” he said.
About Michael Kan
Senior Reporter

Read the latest from Michael Kan

![[K-Beauty] Rose Vitamin Oil to Foam | Daily Face Wash Oil Based Cleanser | Korean Rose Oil Foaming Face Cleanser | Hydrating Facial Cleanser for Dry Sensitive Skin (3.88 oz)](https://i1.wp.com/m.media-amazon.com/images/I/71sX7yIuXRL._SL1500_.jpg?w=300&resize=300,300&ssl=1)





![[ 8 Pack ] Plastic Storage Baskets With Lids, Small Pantry Organization, Stackable Storage Bins, Household Organizers for Cabinets, Countertop, Drawers, Under Sink or On Shelves,Gray](https://i1.wp.com/m.media-amazon.com/images/I/81NMRFDwXYL._AC_SL1500_.jpg?w=300&resize=300,300&ssl=1)
![[Luxury] Kitchen Soap Dispenser Set – 16OZ Black Glass Bottle, Stainless Steel Pump, Instant Dry Tray, Waterproof Labels, Non-Slip Silicone Pad, and Dish Brush | Upgrade for Your Kitchen and Bathroom](https://i3.wp.com/m.media-amazon.com/images/I/71TQcJWiGtL._AC_SL1500_.jpg?w=300&resize=300,300&ssl=1)